Tech
Techoldnewz.in: A Comprehensive Guide to Understanding Technology Trends
Published
7 months agoon

As technology continues to shape every facet of our lives, staying informed about the latest trends and innovations is crucial. Techoldnewz.in has established itself as a go-to source for technology-related news, offering readers insights into the ever-evolving world of technology. In this article, we will provide a detailed analysis of tech trends, ensuring that readers remain ahead of the curve and fully understand the emerging developments.
Table of Contents
The Impact of Artificial Intelligence on Everyday Life
Artificial Intelligence (AI) is no longer a concept of the future—it is now a part of our everyday lives. From smart homes to AI-driven customer service, this technology is becoming deeply embedded in various industries. The rise of machine learning and deep learning is allowing systems to make complex decisions, solve problems, and even improve efficiency across multiple sectors.
For instance, AI-driven algorithms now manage everything from e-commerce recommendations to healthcare diagnostics. In healthcare, AI is used to identify patterns in data that can lead to better patient outcomes. This ability to predict potential issues before they arise is transforming industries, leading to significant savings and improved service quality.
How AI Is Revolutionizing Business Operations
In the corporate world, AI is taking on a pivotal role in reshaping operations. Companies are adopting AI-powered tools for data analytics, customer service, and even robotic process automation (RPA), which automates routine tasks, improving efficiency and reducing human error. AI-driven systems are also capable of enhancing marketing strategies through predictive analytics, providing insights into consumer behavior that allow businesses to target their audiences more effectively.
Blockchain: Beyond Cryptocurrency
While blockchain technology is often associated with cryptocurrency, its potential extends far beyond digital currency. The decentralization of information through blockchain is revolutionizing areas like supply chain management, smart contracts, and data security.
Blockchain’s Role in Enhancing Data Security
One of the most significant applications of blockchain lies in data protection. By decentralizing information and using cryptographic techniques, blockchain offers a new layer of security that is difficult for hackers to breach. In industries such as finance, healthcare, and government, the ability to safeguard sensitive information is paramount, and blockchain is being adopted at an increasing rate to meet this need.
Blockchain is also being used to create secure digital identities, which can significantly reduce the risk of identity theft. This technology allows individuals to take control of their own data, ensuring that it is only shared with trusted parties.
5G Technology: Revolutionizing Connectivity
With the rollout of 5G networks, the world is set to experience a revolution in how we connect and communicate. Offering faster speeds, lower latency, and the capacity to connect billions of devices simultaneously, techoldnewz.in 5G technology promises to transform industries like healthcare, manufacturing, and entertainment.
How 5G Will Transform the Internet of Things (IoT)
One of the biggest beneficiaries of 5G technology is the Internet of Things (IoT). The faster data transmission speeds and reduced latency provided by 5G will allow fortecholdnewz.in more real-time communication between IoT devices. This improvement will enhance smart cities, autonomous vehicles, and industrial automation.
In smart cities, for example, 5G will enable better traffic management, energy efficiency, and techoldnewz.in emergency response systems. Autonomous vehicles will also rely heavily on 5G for instant data sharing, ensuring they can operate safely and efficiently.
The Rise of Quantum Computing
Quantum computing is a game-changing technology that has the potential to solve problems that are currently unsolvable by traditional computers. While still in its infancy, the development of quantum computing could revolutionize industries such as cryptography, drug discovery, and logistics.
Quantum Computing’s Impact on Cryptography
One of the key areas where quantum computing could have a profound impact is cryptography. Traditional encryption methods rely on the difficulty of factoring large numbers, but quantum computers have the potential to solve these problems in a fraction of the time. This breakthrough could lead to the development of quantum-safe encryption methods, ensuring that sensitive data remains secure in the face of this emerging techoldnewz.in.
The Evolution of Cloud Computing
The rise of cloud computing has transformed how businesses operate, providing flexible and scalable solutions for data storage and techoldnewz.in processing. Companies are now able to leverage cloud-based services to reduce costs, improve collaboration, and enhance their disaster recovery capabilities.
Hybrid Cloud: The Best of Both Worlds
Many businesses are now adopting a hybrid cloud approach, combining the benefits of both public and private clouds. This model allows companies to enjoy the scalability of public cloud services while maintaining control over sensitive data by keeping it in a private cloud. The hybrid cloud model offers flexibility, cost savings, and techoldnewz.in making it a popular choice for organizations of all sizes.
The Growing Importance of Cybersecurity
As technology continues to advance, so too does the need for cybersecurity. With the increasing number of devices connected to the internet, the potential for cyberattacks has grown significantly. Businesses and individuals alike must now prioritize techoldnewz.in measures to protect their data from malicious actors.
Top Cybersecurity Threats to Watch
Some of the most pressing cybersecurity threats include ransomware, phishing attacks, and data breaches. Ransomware, in particular, has seen a sharp increase in recent years, with cybercriminals encrypting files techoldnewz.in and demanding payment for their release. Phishing attacks—where attackers attempt to trick individuals into providing sensitive information—continue to be a significant threat as well.
To combat these risks, businesses are investing in advanced cybersecurity tools such as AI-driven threat detection systems and multi-factor authentication (MFA). These techoldnewz.in can help identify and respond to threats in real-time, significantly reducing the potential for damage.
Virtual Reality and Augmented Reality: Transforming Experiences
Virtual Reality (VR) and Augmented Reality (AR) are reshaping how we experience entertainment, education, and even business. With VR, users can immerse themselves in a completely digital environment, while AR overlays digital content onto the real world.
Applications of VR and AR in Various Industries
In entertainment, VR is providing users with fully immersive experiences in gaming and media. Meanwhile, AR is being used in sectors like techoldnewz.in healthcare and retail. For example, surgeons can use AR to overlay important information during procedures, while retailers are using the technology to offer virtual fitting rooms and enhanced product visualization.
Conclusion
Staying updated with the latest technology trends is techoldnewz.in essential in today’s fast-paced world. From the transformative potential of AI, blockchain, and 5G, to the future of quantum computing and the importance of cybersecurity, technology is changing how we live, work, and interact with the world around us. By keeping an eye on these trends, individuals and businesses can ensure they remain competitive and prepared for the future.
Frequently Asked Questions (FAQs)
1. What is Artificial Intelligence (AI) and how is it used today?
AI refers to the simulation of human intelligence in machines. Today, AI is used in a wide range of applications, including smart home devices, customer service chatbots, data analytics, and healthcare diagnostics. AI helps systems make decisions, automate tasks, and improve overall efficiency.
2. What is blockchain technology?
Blockchain is a decentralized and distributed digital ledger that records transactions across many computers. It’s best known for supporting cryptocurrencies like Bitcoin, but it’s also used in supply chain management, secure digital identities, and smart contracts.
3. How does 5G technology improve connectivity?
5G is the fifth generation of mobile networks. It provides faster speeds, lower latency, and supports the connection of many devices simultaneously. This improvement boosts the performance of technologies like autonomous vehicles, IoT devices, and smart cities.
4. What are the potential benefits of quantum computing?
Quantum computing is expected to solve problems beyond the reach of traditional computers, such as advanced cryptography and drug discovery. It processes information in fundamentally different ways, allowing for faster and more complex problem-solving.
5. Why is cybersecurity important?
With the increasing use of digital technologies, the risk of cyberattacks, such as phishing and ransomware, has risen. Cybersecurity protects personal and business data from unauthorized access, ensuring the safety of sensitive information.
6. What’s the difference between Virtual Reality (VR) and Augmented Reality (AR)?
VR immerses users in a fully digital environment, often used in gaming and simulations. AR, on the other hand, overlays digital elements onto the real world, which is useful in industries like retail and healthcare for enhancing real-world experiences.
7. How does AI improve business operations?
AI helps businesses by automating routine tasks, improving decision-making through data analysis, and enhancing customer service. AI-powered tools like robotic process automation (RPA) and chatbots reduce costs and improve efficiency.
8. What industries benefit most from 5G technology?
Industries like healthcare, automotive, and manufacturing benefit greatly from 5G technology due to its ability to support real-time communication, low latency, and high-speed data transfer.
9. How does blockchain enhance data security?
Blockchain secures data by using encryption and distributing it across a decentralized network, making it nearly impossible for hackers to alter. It is particularly useful in industries like finance and healthcare, where data integrity is critical.
10. What are the most common cybersecurity threats today?
Some of the most common cybersecurity threats include ransomware, phishing, and data breaches. These threats can lead to loss of data, financial damage, and reputational harm if not properly managed.
You may like
Tech
The Ultimate Guide to TechandGameDaze.com: Your Premier Destination for Gaming and Technology Insights
Published
3 days agoon
May 4, 2025
Introduction to TechandGameDaze.com
In the ever-evolving world of technology and gaming, staying ahead of trends, updates, and reviews is crucial. TechandGameDaze.com has emerged as a leading platform for enthusiasts, gamers, and tech-savvy individuals seeking accurate, up-to-date, and insightful content. With a focus on everything from game reviews to gadget analysis, this site is designed to keep readers informed and engaged.
Unmatched Gaming Reviews and Walkthroughs
One of the standout features of TechandGameDaze.com is its comprehensive gaming reviews. Whether you’re a fan of AAA blockbusters or indie treasures, this site offers in-depth evaluations, gameplay analysis, and hands-on insights that go beyond surface-level overviews.
We cover:
- Platform-specific performance (PS5, Xbox Series X, PC, Nintendo Switch)
- Graphics and performance metrics
- Narrative depth and character development
- Multiplayer experiences and online performance
- User interface and game mechanics
These reviews are crafted to provide genuine value, helping gamers make informed purchasing decisions and get the most out of their gaming sessions.
Cutting-Edge Tech News and Trends
In the fast-paced world of technology, timely updates and reliable news are essential. TechandGameDaze.com delivers real-time tech news across a variety of industries including:
- Consumer electronics (smartphones, tablets, wearables)
- Artificial Intelligence and Machine Learning
- Virtual Reality and Augmented Reality
- PC hardware and custom builds
- Software updates and cybersecurity threats
Our articles delve into how emerging technologies impact daily life, the economy, and future innovations. With expert analysis, we translate complex topics into digestible content for all levels of readers.
Expert Product Reviews and Buying Guides
We understand the importance of purchasing the right tech and gaming gear. That’s why TechandGameDaze.com provides rigorous, unbiased reviews and comparative buying guides for a wide range of products:
- Gaming consoles and accessories
- Laptops, CPUs, GPUs, and motherboards
- Gaming keyboards, mice, and headsets
- Smart home devices
- Streaming gear and content creation tools
Our buying guides consider factors like performance, durability, compatibility, value for money, and user reviews. We also rank products by budget range, helping you find the best option whether you’re on a tight budget or looking to invest in high-end gear.
Step-by-Step Tutorials and How-To Guides
We don’t just report on new tech—we help users make the most of it. TechandGameDaze.com features a rich archive of how-to guides and DIY tutorials tailored to both beginners and seasoned pros.
Popular tutorials include:
- How to build a gaming PC from scratch
- Optimizing in-game graphics for better performance
- Installing and configuring mods safely
- Securing your network and digital privacy
- Tips for enhancing streaming quality on Twitch and YouTube
These guides are structured step-by-step, with visual aids and clear instructions, ensuring ease of use even for those new to technology or gaming setups.
Community Engagement and Forums
More than just a content hub, TechandGameDaze.com thrives on community interaction. The platform hosts active discussion forums, where users can:
- Share game strategies and tips
- Discuss tech rumors and leaks
- Get help with hardware/software troubleshooting
- Post user reviews and unboxings
This thriving community is moderated to maintain quality and respect, offering a safe space for gamers and tech lovers to connect, collaborate, and grow together.
Upcoming Releases and Event Coverage
Stay ahead of the curve with our calendar of upcoming game releases and technology launches. We provide exclusive previews, hands-on demos, and live coverage of major events including:
- E3 and Gamescom
- CES and Computex
- Apple Events and Google I/O
- Sony State of Play and Nintendo Directs
Our team provides real-time updates, expert commentary, and post-event analysis to ensure you’re never left out of the loop.
Performance Benchmarks and Stress Tests
For tech enthusiasts and gamers who demand the best, TechandGameDaze.com offers detailed benchmark reports and performance tests. These cover:
- Gaming FPS comparisons across platforms
- CPU/GPU temperature and load handling
- SSD vs HDD performance in gaming
- Latency testing for competitive gaming setups
- VR compatibility and smoothness metrics
We use standardized testing environments and transparent methodologies so you can trust the results when planning your next upgrade.
Exclusive Interviews and Industry Insights
We bring you closer to the creators and innovators behind your favorite technologies and games. Through exclusive interviews, developer Q&As, and insider panels, TechandGameDaze.com reveals:
- What inspires game developers
- Behind-the-scenes looks at tech startups
- Future plans for leading brands like NVIDIA, Sony, and Valve
- Industry challenges and opportunities
These features offer unique perspectives and make our platform a bridge between consumers and creators.
Why TechandGameDaze.com Stands Out
While many websites repackage press releases, TechandGameDaze.com is committed to original reporting, critical analysis, and reader-focused content. We uphold:
- Integrity and transparency in product recommendations
- Responsiveness to industry developments
- Commitment to quality over quantity
- Mobile-optimized content for readers on the go
Whether you’re a lifelong gamer, a budding tech reviewer, or just someone looking to stay updated, TechandGameDaze.com is your go-to digital companion.
Conclusion
TechandGameDaze.com continues to establish itself as a premier destination for tech enthusiasts and gamers alike. With its in-depth reviews, up-to-the-minute news coverage, expert guides, and active community engagement, the platform delivers unparalleled value to its audience. Whether you’re diving into the latest AAA title, upgrading your hardware, or exploring emerging technologies, TechandGameDaze.com provides the tools, insights, and support you need to stay ahead of the curve.
By consistently offering well-researched, user-focused content, this site has proven itself a trusted authority in the gaming and tech ecosystem. Bookmark it, subscribe, and become part of a thriving community that shares your passion for innovation and entertainment.
FAQs About TechandGameDaze.com
1. What type of content does TechandGameDaze.com publish?
TechandGameDaze.com publishes a wide variety of content including gaming reviews, technology news, product comparisons, how-to guides, tutorials, and exclusive interviews with industry experts. The site caters to both beginners and advanced users.
2. Is the product review content unbiased?
Yes, all product reviews on TechandGameDaze.com are written with complete transparency. Each item is evaluated based on performance, features, price, user feedback, and real-world use, ensuring readers get honest and useful insights.
3. Does the site cover both gaming and non-gaming tech?
Absolutely. While TechandGameDaze.com is known for its comprehensive gaming coverage, it also offers deep dives into consumer electronics, PC hardware, software, smart gadgets, and other non-gaming technologies.
4. Can I contribute to TechandGameDaze.com?
Yes, the site encourages contributions from tech writers, gamers, and industry experts. If you’re passionate about writing and have relevant experience, you can apply to join their growing team of contributors.
5. Is there a way to get updates on new content?
You can subscribe to the TechandGameDaze.com newsletter to receive regular updates on new articles, guides, and announcements. Notifications for major tech events and game releases are also shared through email and social media.
6. Are the tutorials beginner-friendly?
Yes, the platform offers step-by-step tutorials that are beginner-friendly while also providing advanced-level insights for experienced users. Screenshots, videos, and examples help make the content easy to follow.
7. How often is the website updated?
TechandGameDaze.com is updated daily with fresh content, including breaking tech news, game reviews, editorials, and community polls. The team ensures that readers have access to the latest information at all times.
8. Does the website offer affiliate links?
Yes, the site may include affiliate links to recommended products, but this never influences the editorial integrity of the reviews. Full disclosure is provided, and only high-quality, relevant products are featured.

In the rapidly evolving world of gaming, performance, portability, and innovation define the best gaming laptops. As we step into 2025, the gaming industry demands machines that can handle cutting-edge AAA titles, VR integration, and seamless streaming experiences. We’ve thoroughly researched and compiled the most powerful and reliable gaming laptops that dominate the market this year.
Top Features to Look for in a Gaming Laptop in 2025
Gaming laptops in 2025 come packed with revolutionary features. Here are the key specs and technologies that set elite devices apart:
- Latest GPUs: NVIDIA GeForce RTX 50-series and AMD Radeon RX 8000 series GPUs deliver ray tracing and AI-enhanced rendering.
- High Refresh Rate Displays: 240Hz and 300Hz QHD panels ensure ultra-smooth gameplay.
- Advanced Cooling Systems: Vapor chamber cooling and liquid metal thermal compounds prevent throttling.
- DDR5 RAM and PCIe Gen 5 SSDs: Speed up multitasking and reduce game load times drastically.
- AI-powered Performance Enhancements: Smart tuning optimizes frame rates in real-time.
1. Alienware x17 R4 – The Pinnacle of Performance
CPU: Intel Core i9-14980HX
GPU: NVIDIA RTX 5090
RAM: 64GB DDR5
Storage: 4TB PCIe 5.0 SSD
Display: 17.3” UHD 4K 144Hz
Weight: 3.2 kg
The Alienware x17 R4 remains a behemoth in the gaming arena. Equipped with an RTX 5090, it crushes every title in ultra-settings while staying cool thanks to its Cryo-tech cooling. The immersive 4K screen brings cinematic quality to competitive shooters and story-driven games alike. Built for streamers, creators, and hardcore gamers, the x17 R4 is the ultimate future-proof investment.
2. ASUS ROG Zephyrus M24 – Best Balance of Power and Portability
CPU: AMD Ryzen 9 9955HX
GPU: NVIDIA RTX 5080
RAM: 32GB DDR5
Storage: 2TB SSD
Display: 16” QHD+ 240Hz Nebula HDR
Weight: 1.9 kg
The ROG Zephyrus M24 sets a new benchmark for ultra-portable gaming. This sleek beast merges Ryzen’s raw computing power with a 5080 GPU, all packed into a slim magnesium alloy chassis. Its Nebula HDR display offers rich contrast and vivid color, ideal for both competitive FPS and open-world RPGs. The battery life is class-leading, allowing gamers to stay untethered longer.
3. MSI Titan GT79 – Extreme Performance for Desktop Replacement
CPU: Intel Core i9-14900K
GPU: NVIDIA RTX 5090
RAM: 128GB DDR5
Storage: 8TB RAID 0 SSD
Display: 18” QHD+ 240Hz Mini LED
Weight: 3.8 kg
When only desktop-level performance will do, the MSI Titan GT79 answers the call. This powerhouse caters to gamers who demand maximum specs with no compromise. The RTX 5090, paired with an overclockable desktop CPU, annihilates rendering tasks and 8K video workflows. It’s heavy, yes—but for streamers and developers, it’s a dream machine.
4. Razer Blade 16 – Sleek and Stunning Performance
CPU: Intel Core i9-14950HX
GPU: NVIDIA RTX 5080
RAM: 32GB DDR5
Storage: 2TB SSD
Display: 16” Dual-Mode Mini LED UHD+ / FHD+ 240Hz
Weight: 2.1 kg
Razer continues its tradition of minimalist design and top-tier specs with the Blade 16. The innovative dual-mode display lets users toggle between UHD+ 120Hz for content and FHD+ 240Hz for esports. Its aluminum body remains one of the most premium in class. Perfect for gamers and content creators, it balances aesthetics and raw power like no other.
5. Lenovo Legion 9i – AI-Powered Gaming Excellence
CPU: Intel Core i9-14980HX
GPU: NVIDIA RTX 5080
RAM: 64GB DDR5
Storage: 2TB Gen 5 SSD
Display: 16” 3.2K 165Hz Display
Weight: 2.3 kg
Lenovo’s Legion 9i integrates real-time AI enhancements to optimize gameplay dynamically. Built-in sensors adjust power and cooling based on player behavior. With robust specs and a spectacular 3.2K display, the Legion 9i offers ultra-smooth visuals, whisper-quiet operation, and a uniquely gamer-centric design. Great for users who value intelligent performance tuning.
6. HP Omen Transcend 16 – Budget-Friendly Beast
CPU: AMD Ryzen 9 9900HS
GPU: NVIDIA RTX 4070
RAM: 32GB DDR5
Storage: 1TB SSD
Display: 16” QHD 240Hz
Weight: 2.0 kg
For gamers seeking maximum value without sacrificing power, the HP Omen Transcend 16 stands out. It offers excellent 1440p gaming with ray tracing capabilities, fast boot times, and a responsive keyboard. Its sleek design and accessible pricing make it one of the best mid-tier gaming laptops of 2025.
Emerging Technologies Defining 2025 Gaming Laptops
1. AI Optimization
Many 2025 laptops now use AI algorithms to enhance FPS, allocate system resources intelligently, and monitor thermal performance in real time. This ensures consistent frame delivery and battery longevity.
2. Dual-Display Integration
Gaming laptops like the ASUS Zenbook Duo series are now incorporating secondary touch displays, aiding streamers and multitaskers with real-time chat, system monitoring, and productivity tools.
3. Integrated Game Streaming Features
Built-in camera enhancements, virtual backgrounds, and live audio tuning make laptops fully capable of professional-grade streaming—no external accessories required.
How to Choose the Best Gaming Laptop in 2025
Before purchasing, assess the following:
- What games do you play? Fast-paced titles demand high refresh rates and top-tier GPUs.
- Do you stream or create content? Choose models with powerful CPUs and dedicated encoding chips.
- How mobile are you? Slim models like Zephyrus M24 or Razer Blade 16 balance portability and power.
- What’s your budget? Mid-range options with RTX 4060/4070 GPUs still deliver superb 1080p or 1440p gaming.
Conclusion: Dominate 2025 Gaming with the Right Laptop
The best gaming laptops of 2025 combine raw power, intelligent design, and advanced cooling to deliver unmatched experiences. Whether you’re an esports competitor, a 3D artist, or a casual gamer, there’s a machine tailored to your needs. These laptops aren’t just about gaming—they’re full-fledged multimedia powerhouses for the future.

Introduction
In both photography and cinematography, light plays a pivotal role in shaping the mood, tone, and visual storytelling of an image. Among the many phenomena that can occur when light interacts with a camera lens, one of the most intriguing—and sometimes polarizing—is lens flare. Whether it’s viewed as a distracting imperfection or an artistic flourish, lens flare has become a recognizable and influential element in visual media.
This article explores what lens flare is, how it occurs, its types, its impact on visual composition, and how it’s used intentionally in art and film.
What is Lens Flare?
Lens flare is a visual artifact that occurs when a strong light source—typically the sun or an artificial light—shines directly into a camera lens, causing internal reflections and scattering of light within the lens system. This results in bright spots, circles, or streaks of light that may appear across the image. These artifacts can vary in color, shape, and intensity depending on the lens design and angle of light.
The Physics Behind Lens Flare
To understand lens flare, it’s essential to understand the optical design of a camera lens. Modern lenses are composed of multiple glass elements arranged in groups. Each surface of these elements has the potential to reflect a small portion of the incoming light. When a bright light source hits the lens, some light reflects off these internal surfaces and bounces around inside the lens housing.
There are two main types of flare:
- Specular Flare (Ghosting): These are distinct, geometric shapes—often hexagons or circles—that mirror the shape of the aperture. They appear in a sequence or arc pattern across the image.
- Veiling Flare: A more diffuse, foggy light that reduces contrast and washes out parts of the image, giving it a dreamy or overexposed look.
Factors that influence lens flare:
- Lens coatings: High-quality anti-reflective coatings reduce flare.
- Number of lens elements: More elements can increase the risk of internal reflections.
- Lens hoods: Designed to block stray light and reduce flare.
- Aperture shape: Affects the shape of the flare artifacts.
Lens Flare in Photography
In photography, lens flare is often considered both a technical flaw and a creative opportunity. Traditional photographers strive to minimize lens flare to maintain high contrast and clarity in their images. However, artistic photographers sometimes use flare to add warmth, emotion, or a sense of spontaneity.
Common uses in photography:
- Backlit portraits: A flare can create a soft halo around the subject, emphasizing warmth and intimacy.
- Nature photography: Sun flares can add a magical quality to landscapes.
- Street and lifestyle photography: Flares introduce a sense of realism and imperfection, giving images a raw or nostalgic feel.
Lens Flare in Film and Cinematography
In cinema, lens flare has become a stylistic signature for certain filmmakers, particularly in action, sci-fi, and drama genres.
Notable Directors and Films:
- J.J. Abrams: Known for his excessive use of lens flares in films like Star Trek (2009), which sparked both admiration and parody. Abrams used anamorphic lenses to intentionally create prominent blue horizontal flares.
- Steven Spielberg: Often used flare in natural lighting situations, particularly in E.T. and Close Encounters of the Third Kind.
- Terrence Malick: Used flares artistically to enhance the spiritual and poetic tone in films like The Tree of Life.
Lens flare in films can symbolize:
- Hope and transcendence: A glowing flare around a character can suggest revelation or divinity.
- Chaos and disorientation: In action scenes, flares can increase visual tension.
- Futurism and sci-fi: Blue-tinted flares add a sleek, technological aesthetic.
Digital Lens Flare: Post-Production and CGI
With the rise of digital filmmaking and editing tools, lens flares can now be added or removed in post-production. Software like Adobe After Effects, Final Cut Pro, and DaVinci Resolve offer built-in tools or plugins (such as Red Giant’s Optical Flares) to create realistic or stylized flares.
In video games and CGI-heavy films, lens flares are used to simulate the effect of a “virtual camera” to enhance realism or mimic a specific cinematic style.
However, artificial lens flare must be used with care. Overuse or poor integration can break immersion or feel gimmicky.
How to Create or Control Lens Flare
If you’re a photographer or filmmaker looking to experiment with lens flare, here are some tips:
To Create Flare:
- Shoot toward the sun or a strong light source.
- Remove the lens hood.
- Use a wide aperture to create dramatic circular flares.
- Try vintage or uncoated lenses for more unpredictable results.
To Avoid or Minimize Flare:
- Use a lens hood.
- Shade your lens with your hand or another object.
- Invest in high-quality lenses with advanced coatings.
- Adjust your shooting angle to keep the light source out of the frame.
The Cultural Impact of Lens Flare
Lens flare has evolved from a technical nuisance into a visual language. It now carries symbolic and emotional weight in modern media. From the spiritual haze of Malick’s landscapes to the futuristic sheen of Abrams’ starships, lens flare is a testament to how imperfections can become iconic.
Even in pop culture, lens flare is widely recognized. It’s been used in memes, video game HUDs, and stylized social media posts. While some audiences critique its overuse, others embrace it as a mark of cinematic flair.
Conclusion
Lens flare is more than just a product of physics—it’s an aesthetic choice. What once began as an optical error is now a tool that photographers and filmmakers use to express mood, authenticity, and imagination. Whether you’re shooting a sun-drenched landscape or crafting a sci-fi epic, lens flare remains a powerful way to shape how light—and emotion—moves through your frame.
Trending
-

 Blog9 months ago
Blog9 months agoUnderstanding the Impact of Dirtyship on Digital Content: A Comprehensive Guide
-
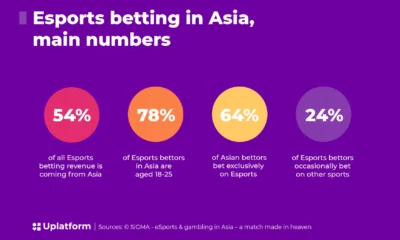
 Sports10 months ago
Sports10 months agoK7反波胆: Revolutionizing Sports Entertainment and Betting in Asia
-

 Games10 months ago
Games10 months agoBаіdurs Gаtе 3:Exploring the Epic Fantasy
-

 Tech8 months ago
Tech8 months agoTechnorozen: A Comprehensive Look at an Innovative Tech Firm
-

 Tech9 months ago
Tech9 months agoExploring Tex9.net: A Comprehensive Overview
-

 App10 months ago
App10 months agoIbomma: Revolutionizing Movie Streaming in India
-

 Entertainment9 months ago
Entertainment9 months agoATFbooru: A Comprehensive Guide to the Imageboard and Its Community
-

 Sports10 months ago
Sports10 months agoBaldezinho: Celebrating Brazilian Street Soccer Culture
